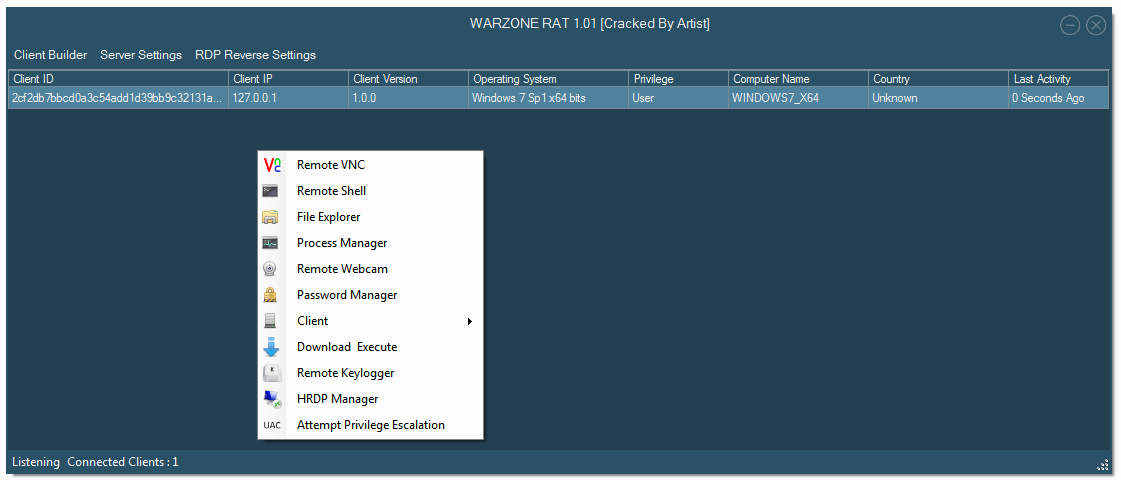
NovoBot C++ HTTP Botnet
NovoBot C++ HTTP Botnet
They are using TDL (Turla Driver Loader) to bypass Windows x64 Driver Signature Enforcement, compiled binaries, they dont even bother to C+P the code. For the UAC bypass they are using UACme, also compiled binaries stored in resources.
HTTP communication with web-panel
UAC Bypass
Ring0 Kit:
Hidden Process
Hidden File
Hidden Startup
Ring0 kit results in hidden process, hidden file, hidden startup.
It gets activated on Windows XP, vista, 7, 8, 8.1 and 10 Preview (up to 1150 build). On latest Windows 10 bot works without activating it.NoboBot comes with a web-panel.
I will setup it for you if needed. It is very easy to setup.It has been coded in C++
It does not need .net framework.(This is the original description)In short:
This is a botnet that is made in the form of a driver, and that is why it starts working after a system restart, and therefore it bypasses UAC.
Hidden autoload
Hidden process
Hidden file
Has no dependencies, as it is written in C ++
UAC Bypass
Ring0 Kit:
Hidden Process
Hidden File
Hidden Startup
It gets activated on Windows XP, vista, 7, 8, 8.1 and 10 Preview (up to 1150 build). On latest Windows 10 bot works without activating it.NoboBot comes with a web-panel.
I will setup it for you if needed. It is very easy to setup.It has been coded in C++
It does not need .net framework.(This is the original description)In short:
This is a botnet that is made in the form of a driver, and that is why it starts working after a system restart, and therefore it bypasses UAC.
Hidden autoload
Hidden process
Hidden file
Has no dependencies, as it is written in C ++
ICQ:653580170
Whatsapp +79017473945
jabber: russianhackerclub@jabber.ru
Whatsapp +79017473945
jabber: russianhackerclub@jabber.ru

![discord SPY TOOL [CRACKED]](https://image.ibb.co/e2UrRp/Screenshot_3.png)