Zeus Botnet 2.0.8.9
Zeus Botnet 2.0.8.9

Zeus Botnet 2.0.8.9
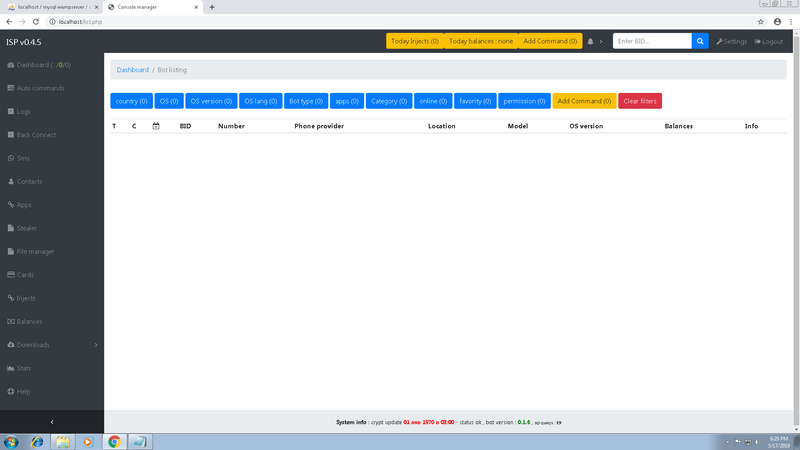
Asacube Android banking Botnet+Tutorial
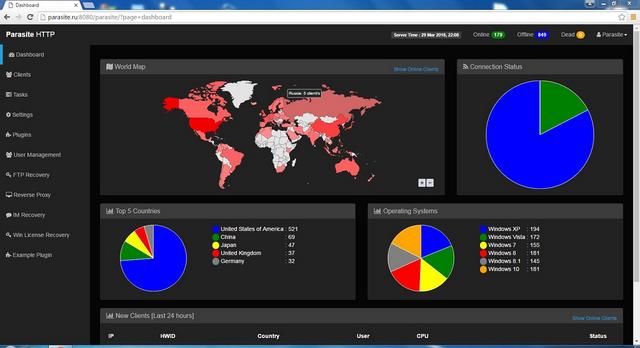
Parasite HTTP Botnet – All Plugins
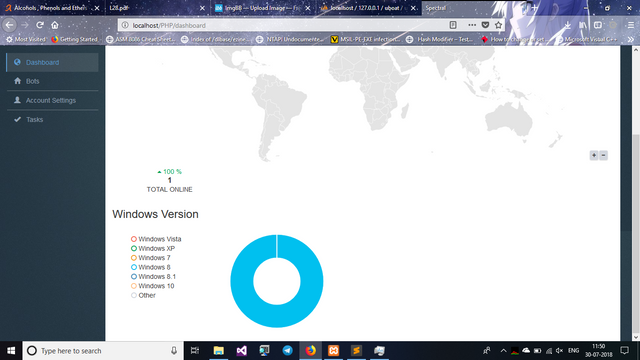
UBoat HTTP Botnet
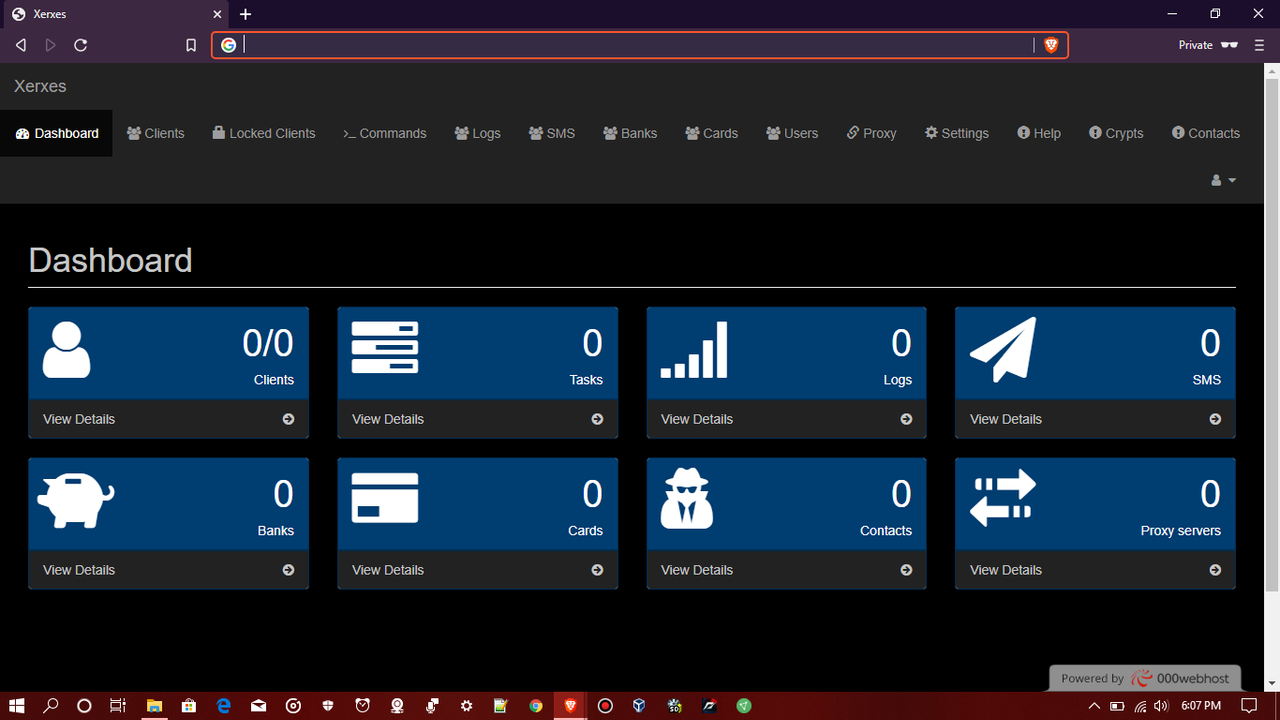
XERXES ANDROID BANKING BOTNET
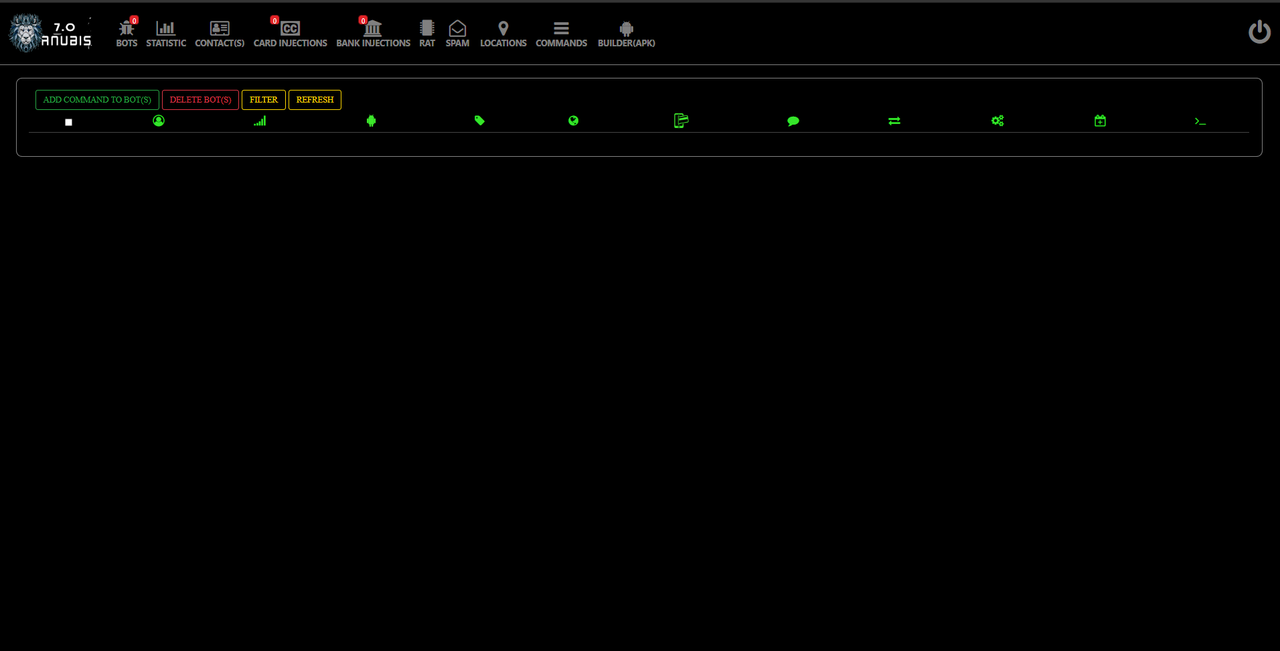
ANUBIS 7.0 ANDROID BOTNET (Panel + Builder+ Tutorial)
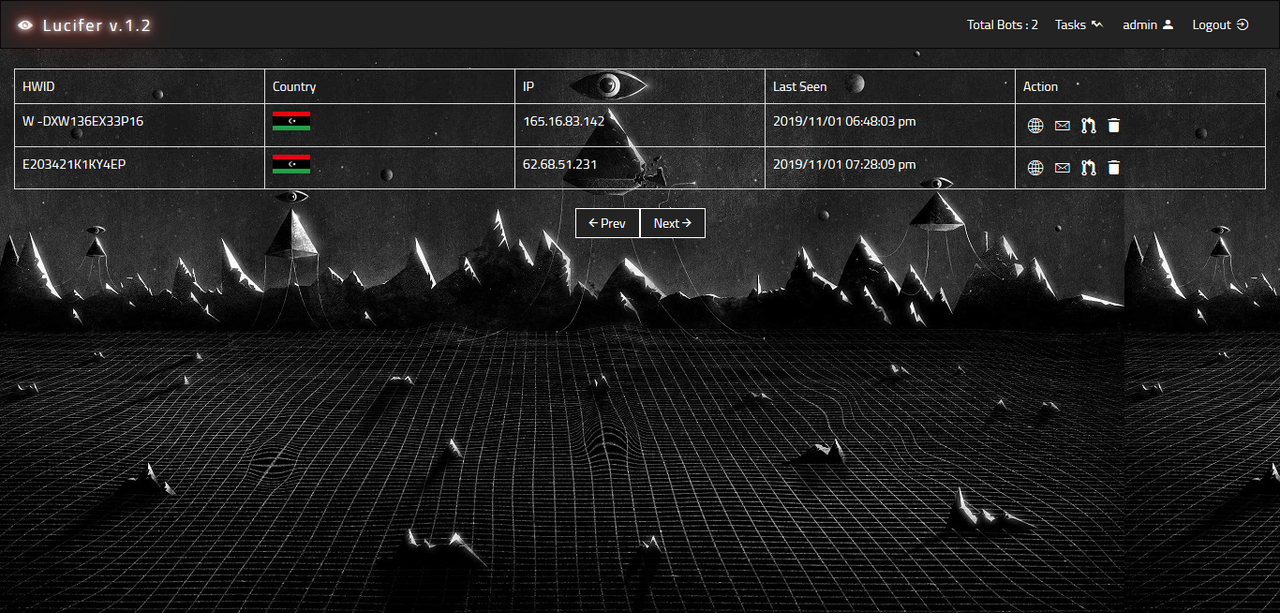
Lucifer v.1.2 HTTP Botnet

NovoBot C++ HTTP Botnet
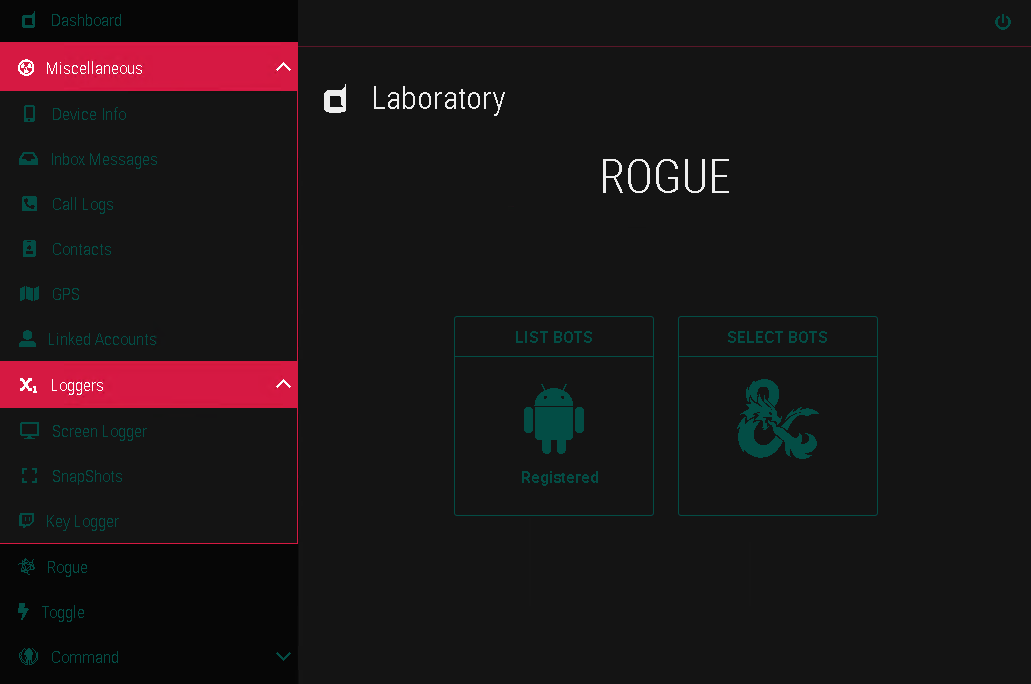
ROGUE V6.2 ANDROID BOTNET PREMIUM
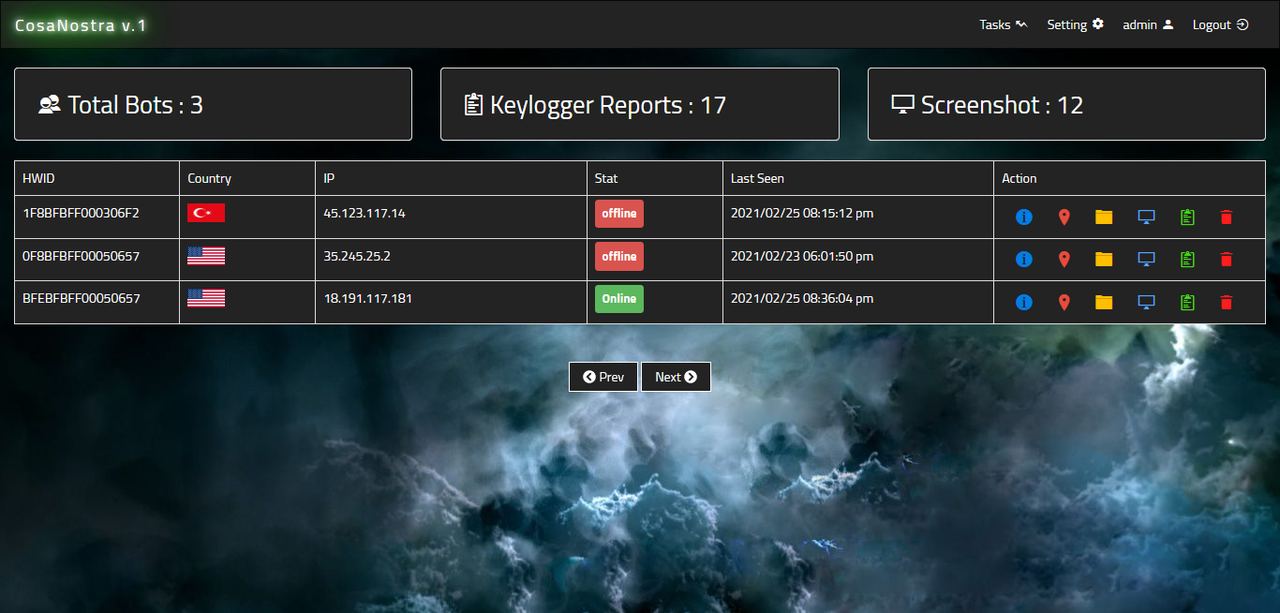
CosaNostra v1.2 HTTP BotNet + Tutorial
End of content
End of content