Anubis 8.0
Anubis 8.0
In the modern era, the digital landscape has revolutionized the way we communicate, conduct business, and interact with the world. However, this immense progress has also brought about new challenges in the form of cyber threats. One such menacing entity that has attracted considerable attention is the Anubis Botnet. This essay delves into the intricacies of the Anubis Botnet, its impact, operation, and the measures required to mitigate its effects.
Understanding the Anubis Botnet:
The Anubis Botnet is a formidable example of how cybercriminals exploit technology for malicious intent. Named after the ancient Egyptian god associated with mummification and the afterlife, the botnet is designed to steal sensitive information from infected devices and perpetrate various cybercrimes. Anubis first came to light around 2017, and it rapidly gained notoriety due to its sophisticated techniques and ability to evolve.
Operation and Techniques:
Anubis operates as a banking trojan, targeting primarily financial institutions and their customers. The botnet typically infects devices through malicious emails, fake websites, or compromised software downloads. Once infected, the malware establishes a connection with a command-and-control server operated by the cybercriminals. This connection allows hackers to remotely control the compromised devices and carry out their nefarious activities.
Anubis employs various techniques to steal sensitive information, such as login credentials, credit card details, and personal information. It can capture screenshots, record keystrokes, and even hijack SMS messages to bypass two-factor authentication. This multi-faceted approach makes Anubis a highly potent threat in the realm of cybercrime.
Impact and Consequences:
The impact of the Anubis Botnet is profound and far-reaching. Individuals and businesses alike fall victim to its schemes, suffering financial losses and reputational damage. Financial institutions face the risk of customer data breaches, leading to not only monetary losses but also a loss of customer trust. Moreover, the collective impact of botnets like Anubis on the global economy is significant, as cybercrimes result in billions of dollars in losses annually.
Mitigation and Prevention:
Addressing the threat posed by the Anubis Botnet and similar cyber threats requires a multi-pronged approach:
- Education and Awareness: Regular cybersecurity training and awareness campaigns can help individuals and organizations recognize phishing attempts, malicious links, and suspicious downloads.
- Robust Security Measures: Employing strong, up-to-date security software can help detect and block malware before it infects devices. Firewalls, intrusion detection systems, and antivirus programs are crucial components of this defense.
- Patch Management: Ensuring that operating systems and software are updated regularly with the latest security patches can prevent vulnerabilities that botnets exploit for infiltration.
- Network Segmentation: Segregating networks can contain the spread of malware within an organization, minimizing potential damage.
- Behavioral Analysis: Employing behavioral analysis tools can identify abnormal patterns of activity, helping to identify infected devices.
- Collaboration: International cooperation between governments, law enforcement agencies, and cybersecurity firms is vital in identifying and apprehending the perpetrators behind botnets like Anubis.
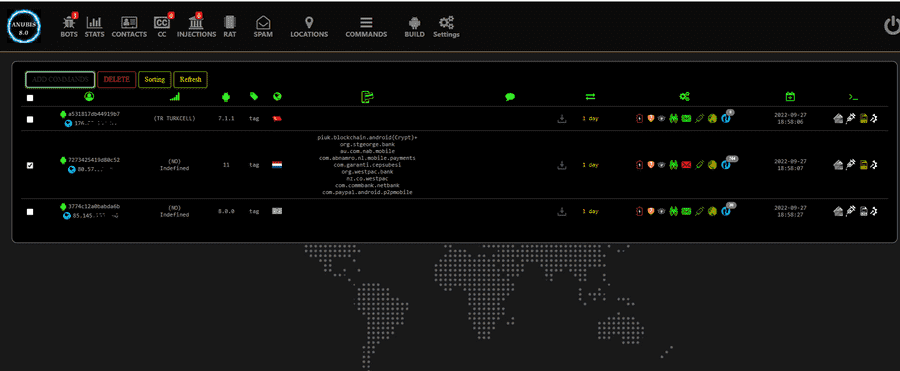
Anubis 8.0 Android RAT
1-RAT,
2-SPAM SMS,
3-GET FULL CONTACT AND SEND SMS,
4-GET ALL SMS,
5-READ ALL SMS,
6-READ ALL APPLICATIONS INSTALLED,
7-IF BANKING SERVICE IS ACTIVE, YOU CAN SEE ALL BANK APPLICATIONS,
8-REMOVE FROM PANEL AND UNINSTALL RAT (IF YOU WANT),
9-OPEN URL IN WEB BROWSER OR HIDDEN BROWSER,
10-SOCKS5 CONNECTIONS,
11-GET BANK INFO WITH MORE INJECTION,
Whatsapp +79017473945