What is Core RDP VIP Scanner?

Core RDP VIP Scanner is a software tool that automates the process of scanning IP addresses for open RDP ports (typically TCP 3389) and attempting to brute-force login credentials. It is often promoted as an “all-in-one” solution for identifying vulnerable RDP servers, extracting IP lists, and testing username-password combinations to gain unauthorized access. The tool integrates with other utilities, such as Nmap, to enhance its scanning capabilities.
The scanner is typically distributed through file-sharing platforms and hacking forums, often accompanied by tutorials detailing its setup and operation. While it is marketed for “cracking and brute-forcing RDPs,” its use is controversial due to its potential for malicious exploitation.
How Does Core RDP VIP Scanner Work?
The tool operates in a multi-step process, combining network scanning and brute-force techniques. Below is an overview of its typical workflow, based on publicly available descriptions:
1. Preparation and Setup
Required Tools: Users need WinRAR to extract the tool’s files and Nmap for network scanning.
Installation: After downloading the scanner, users extract the package and navigate to the “all-in-one scanner” directory. Nmap must be installed to enable IP scanning.
2. Scanning for RDP IPs
Users run a batch file (e.g., blah.bat) that leverages Nmap scripts to scan for IP addresses with open RDP ports.
The scan identifies systems listening on port 3389, which is the default for RDP.
Once sufficient IPs are collected, they are copied for use in the brute-forcing phase.
3. Brute-Forcing Credentials
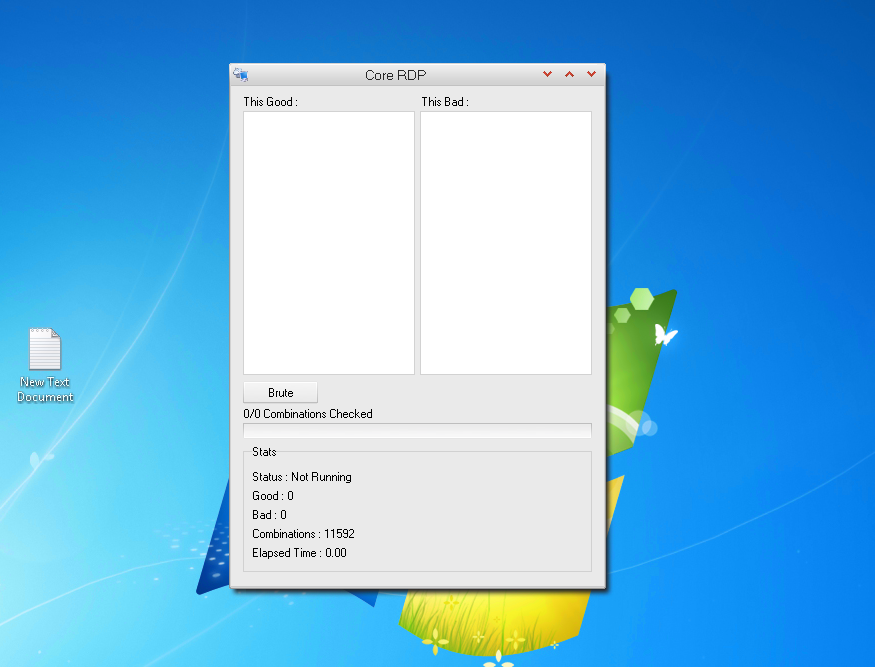
The Core RDP Scanner interface allows users to paste the list of scanned IPs.
Users click “Create List” to initiate the brute-force process, which tests combinations of usernames and passwords against the target IPs.
The tool categorizes results into “Good” (successful logins) and “Bad” (failed attempts) columns, indicating which credentials worked.
4. Output and Access
Successful credentials are displayed in the “Good” column, allowing users to attempt connections to compromised systems using tools like xfreerdp.
The tool is designed to be user-friendly, with a straightforward interface that automates much of the process.
Ethical and Legal Considerations
While Core RDP VIP Scanner may be presented as a tool for penetration testing or security research, its primary use in hacking forums is associated with unauthorized access to systems. This raises significant ethical and legal concerns:
Unauthorized Access: Using the tool to scan or brute-force systems without explicit permission is illegal in most jurisdictions and violates laws such as the U.S. Computer Fraud and Abuse Act (CFAA) or the EU’s Cybersecurity Directive.
Security Risks: Tools like Core RDP VIP Scanner are often distributed through untrusted sources, increasing the risk of malware infection for users.
Impact on Victims: Successful brute-forcing can lead to data breaches, ransomware deployment, or system compromise, causing financial and reputational damage to individuals and organizations.
Security professionals advocate for ethical alternatives, such as conducting authorized penetration tests with tools like Metasploit or Hydra, which can simulate brute-force attacks in a controlled environment. Additionally, organizations can protect against RDP brute-force attacks by implementing strong passwords, account lockout policies, and non-default RDP ports.