Cyborg Keylogger 2025

In the ever-evolving landscape of cybersecurity, keyloggers remain one of the most controversial tools. Among them, the Cyborg Keylogger has gained attention for its stealth and versatility. This article explores what the Cyborg Keylogger is, how it works, its potential uses, and the ethical and legal implications surrounding it.
What is the Cyborg Keylogger?
The Cyborg Keylogger is a software-based tool designed to record keystrokes on a computer or device without the user’s knowledge. Unlike hardware keyloggers, which require physical installation, Cyborg operates entirely in the digital realm, making it harder to detect. It is often marketed as a monitoring tool for legitimate purposes, such as parental control or employee surveillance, but its capabilities also make it a favorite among malicious actors.
Key features of the Cyborg Keylogger include:
Stealth Mode: Runs silently in the background, invisible to most antivirus programs.
Comprehensive Logging: Captures keystrokes, clipboard data, screenshots, and even webcam activity.
Remote Access: Sends collected data to a remote server or email, allowing real-time monitoring.
Cross-Platform Compatibility: Works on Windows, macOS, and some Linux distributions.
How Does It Work?
Once installed, the Cyborg Keylogger embeds itself into the operating system, often disguising itself as a legitimate process. It hooks into the keyboard input stream, capturing every key pressed by the user. Advanced versions may also:
Log browser activity, including URLs visited and form data.
Take periodic screenshots to provide context for the keystrokes.
Record audio or video if the device has a microphone or webcam.
The collected data is encrypted and sent to a predetermined destination, such as an email address or a cloud server controlled by the operator. This makes it particularly dangerous in unauthorized hands, as sensitive information like passwords, credit card numbers, or personal messages can be intercepted.
Legitimate Uses
While often associated with malicious intent, the Cyborg Keylogger has legitimate applications:
Parental Monitoring: Parents can use it to track their children’s online activity, ensuring they avoid harmful content or interactions.
Employee Surveillance: Businesses may deploy keyloggers to monitor employee productivity or prevent data leaks, though this is heavily regulated in many jurisdictions.
Personal Backup: Some users install keyloggers to recover lost data, such as unsaved documents or forgotten passwords.
The Dark Side
The same features that make the Cyborg Keylogger useful for monitoring also make it a potent tool for cyberattacks. Hackers can deploy it through phishing emails, malicious downloads, or compromised websites. Once installed, it can steal:
Login credentials for banking or social media accounts.
Confidential business information.
Personal data for identity theft.
Its stealth capabilities mean victims may remain unaware of the breach for months, amplifying the damage. In 2023, cybersecurity reports noted a rise in keylogger-based attacks, with tools like Cyborg being used in targeted campaigns against small businesses and individuals.
Ethical and Legal Implications
The use of keyloggers, including Cyborg, is a legal gray area. In many countries, installing a keylogger without explicit consent is illegal and can result in severe penalties. For example:
In the United States, the Electronic Communications Privacy Act (ECPA) prohibits unauthorized interception of electronic communications.
In the European Union, GDPR imposes strict rules on monitoring software, requiring transparency and consent.
Ethically, the use of keyloggers raises questions about privacy and trust. Even in legitimate scenarios, such as workplace monitoring, employees may feel violated if not informed. The potential for abuse underscores the need for clear policies and oversight.
Silent Features:
Most advanced remote keylogger
Up-to-date remote password recovery manager
Undetected by major antivirus companies
Eye friendly log format
User friendly interface
Completely customizable
Highly stable and fast
Supports manipulation of client’s server file
Several add-on features
Detailed list of features:
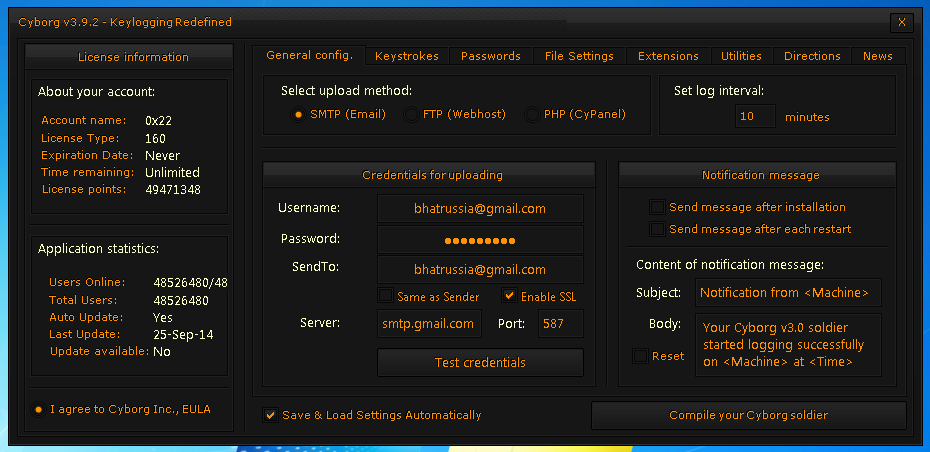
Upload methods: SMTP (Email), FTP (Website), PHP (Webpanel)
Customizable keystroke log interval
Custom notification message
Information about computer included
HTML designed logs
Hot Logs : Record keystrokes on specific windows only
Screenshot logger with variable image formats
Customizable screenshot log interval
Clipboard text logger with customizable title
Customizable clipboard log interval
Fully loaded password recovery manager
Customizable password recovery log interval
Start logging after windows restart
Wait for some time before execution
Bloat file size to your preferred size
File assembly information manipulator
Random assembly information generator
File binder supporting files of all extensions
Process mutex to ensure single instance of execution
Completely customizable fake error message options
Multiple engine antivirus scanner to check detection status
Extension changer and extension spoofer
Clean your computer from Cyborg servers
News system to keep you updated about Cyborg’s happenings
Save and load settings automatically
Protected using NetSeal licensing system with automatic updates
Password Recovery Functions:
Browsers:
Mozilla Firefox
Google Chrome
Internet Explorer
Safari for Windows
Opera for Windows
Messengers:
Beyluxe
IMVU
Trillian
Paltalk
Pidgin
Nimbuzz
Digsby
Miranda
Miscellanious:
Filezilla
Incredimail
No-IP
FTP Commander
Internet Download Manager
DynDNS
jDownloader
CD Keys
Windows Key
Conclusion
The Cyborg Keylogger is a powerful tool with both legitimate and malicious applications. Its ability to operate undetected makes it a significant threat in the wrong hands, but it can also serve as a valuable asset for monitoring in controlled, consensual environments. As with any technology, its impact depends on how it’s used. By understanding its capabilities and taking proactive measures, individuals and organizations can mitigate risks while navigating the complex ethical landscape of digital surveillance.