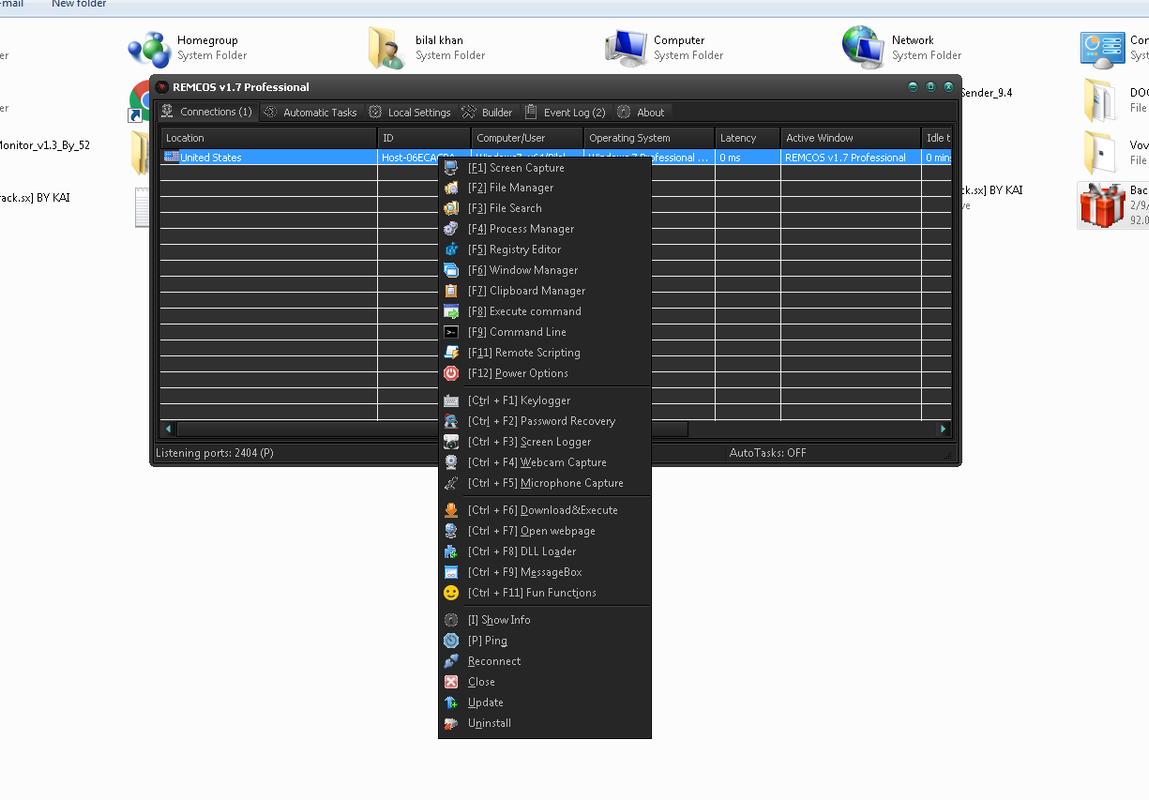
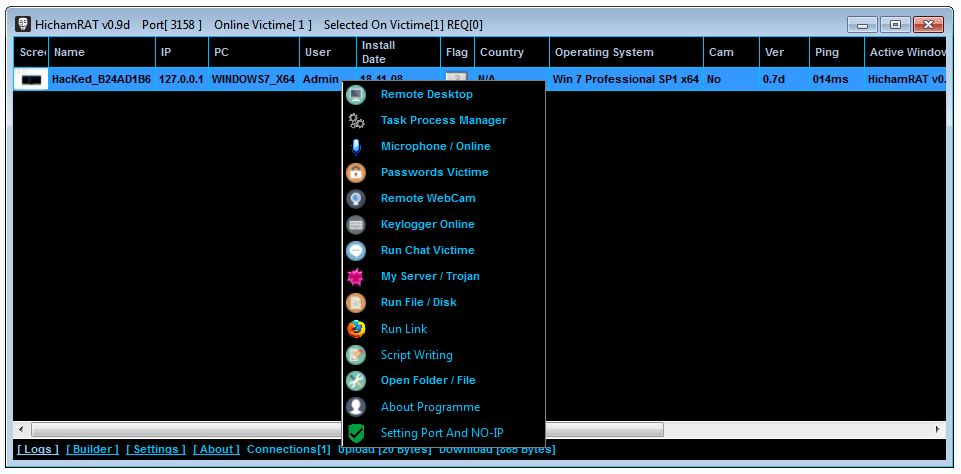
Fenix Clipper Wallets + Auto-Run + Hiden Installer + ByPass Antiviruses
Fenix Clipper Wallets + Auto-Run + Hiden Installer + ByPass Antiviruses
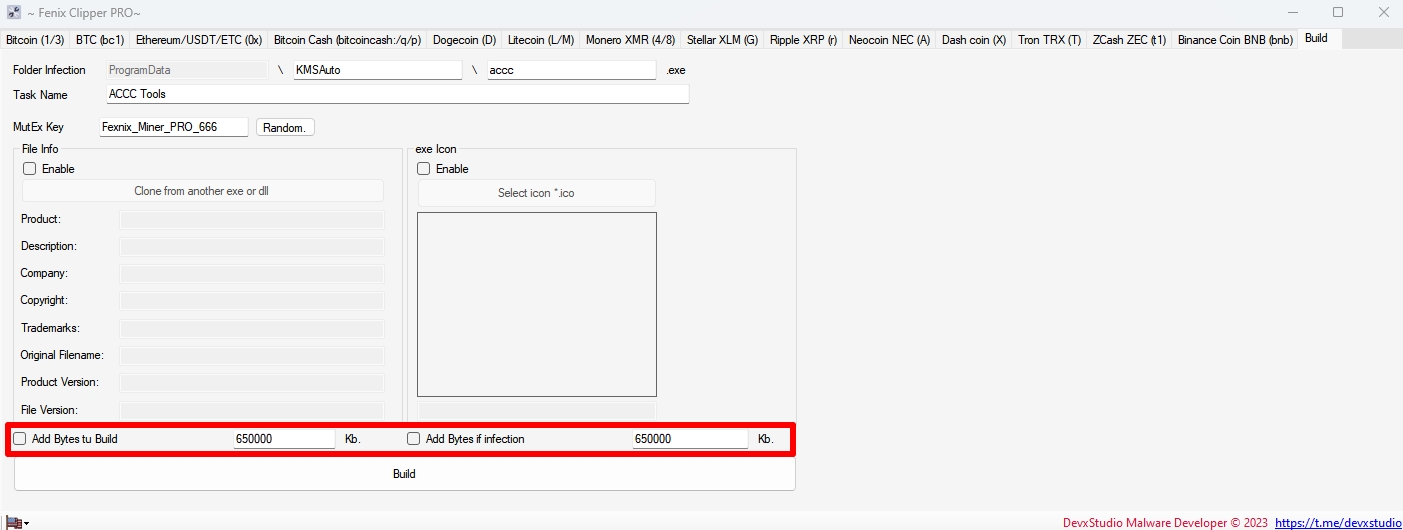
Clipper is written in C# and replaces it with the most similar one by the first and last characters from your list of wallets. It has a hidden installation in the system, auto-loading and bypassing popular antiviruses, it is removed from the place of the initial launch.
Cryptocurrency has been in the news for years now. While it has been lauded for its potential to revolutionize the financial industry, it has also been associated with various risks and dangers. One such threat is crypto malware.Crypto malware is a type of malware that infects a user’s computer or device and uses its processing power to mine cryptocurrency. It can also steal a user’s cryptocurrency wallet or credentials, which can result in the loss of all their digital assets.
There are various types of crypto malware, but they all have the same goal: to generate cryptocurrency for the attacker at the expense of the victim. Let’s take a closer look at some of the most common types of crypto malware.
Cryptojacking
Cryptojacking is the most common type of crypto malware. It infects a user’s computer or device and uses its processing power to mine cryptocurrency. The attacker doesn’t need the victim’s wallet or credentials for this type of attack. They simply need to infect the user’s computer or device and start mining cryptocurrency.
Cryptojacking can go undetected for a long time because it doesn’t cause any noticeable harm to the user’s computer or device. However, it can slow down the system, increase electricity bills, and reduce the lifespan of the hardware.
Ransomware
Ransomware is a type of malware that encrypts a user’s files and demands a ransom in exchange for the decryption key. In some cases, the attacker may demand payment in cryptocurrency. This type of attack can be devastating because it can result in the loss of important data and financial loss.
Trojan
A Trojan is a type of malware that disguises itself as a legitimate program or file and tricks the user into downloading and installing it. Once installed, the Trojan can perform various malicious activities, including stealing a user’s cryptocurrency wallet or credentials.
Phishing
Phishing is a type of social engineering attack that involves tricking the user into revealing their login credentials or other sensitive information. The attacker may send an email or message that appears to be from a legitimate source, such as a cryptocurrency exchange or wallet provider. The user is then directed to a fake website where they are asked to enter their login credentials, which are then stolen by the attacker.
Protecting Yourself from Crypto Malware
Now that we’ve looked at some of the most common types of crypto malware, let’s explore some ways to protect yourself from these attacks.
Keep your software up-to-date
Crypto malware often exploits vulnerabilities in outdated software. To prevent this, it’s important to keep your operating system and all your applications up-to-date. This will ensure that any known vulnerabilities are patched and that your system is more secure.
Use strong passwords
Strong passwords can help prevent brute-force attacks, where the attacker tries to guess your password by using various combinations of characters. Use a combination of uppercase and lowercase letters, numbers, and symbols to create a strong password that is difficult to guess.
Enable two-factor authentication
Two-factor authentication (2FA) adds an extra layer of security to your login process. With 2FA enabled, you will need to provide a second form of authentication, such as a code sent to your phone or a biometric scan, in addition to your password. This makes it much more difficult for attackers to gain access to your account.
Use a reputable antivirus software
A good antivirus software can help detect and remove crypto malware from your system. It can also help prevent future infections by blocking malicious websites and attachments.
Be wary of unsolicited messages
Be cautious of unsolicited emails or messages, especially if they contain links or attachments. Do not click on any links or download any attachments unless you are sure they are from a legitimate source.
Bitcoin – 1*** 3*** bc1***
Ethereum All Tokens – 0x***
All Tokens, USDT, ETC…
Monero – 4*** 8***
Stellar – G***
Ripple – r***
Neocoin – A***
Bitcoin Cash – bitcoincash:*** q*** p***
Dogecoin – D***
Litecoin – M*** L***
Dashcoin – X***
Tron – T***
ZCash – t1***
Binance – bnb***
Whatsapp
Discord: blackhatrussiaofficial#5904
Telegram: https://t.me/adrikadi