Shark Crypto Clipper
Shark Crypto Clipper
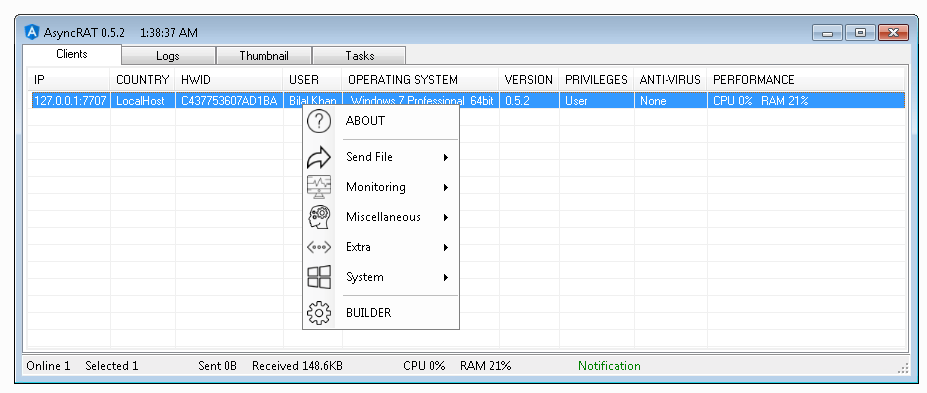
Data Theft: Attackers can use RATs to steal sensitive information, such as login credentials, personal files, or financial data, from the victim’s computer.
Surveillance: RATs can be used to monitor a victim’s activities, including keystrokes, screen captures, and webcam feeds, without the victim’s knowledge or consent.
System Manipulation: Attackers can execute commands on the compromised system, allowing them to install or uninstall software, modify settings, or even take control of the victim’s computer.
Distributed Denial of Service (DDoS) Attacks: Some RATs can be used to coordinate a network of compromised computers to launch DDoS attacks against specific targets.
Propagation: RATs often have the capability to spread to other computers or devices within a network, potentially allowing the attacker to compromise an entire network.
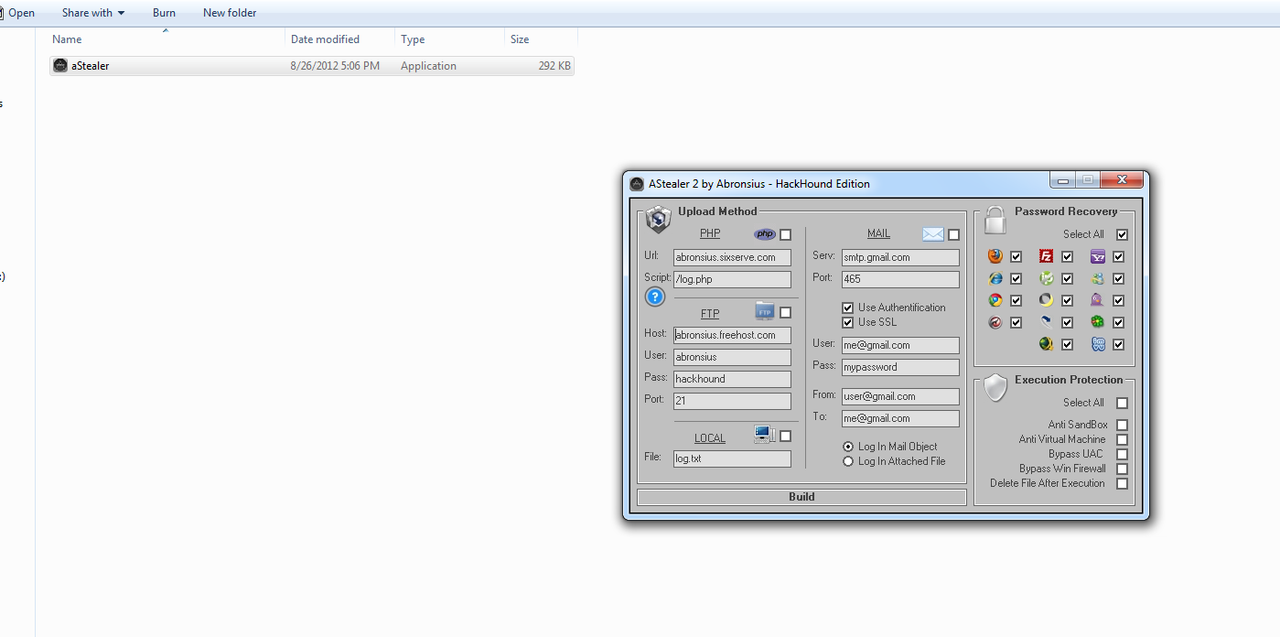
RATs can be delivered through various means, including malicious email attachments, infected software downloads, or drive-by downloads from compromised websites. Once installed on a victim’s system, they typically run in the background, making them difficult to detect.
Get Info
Desktop Access
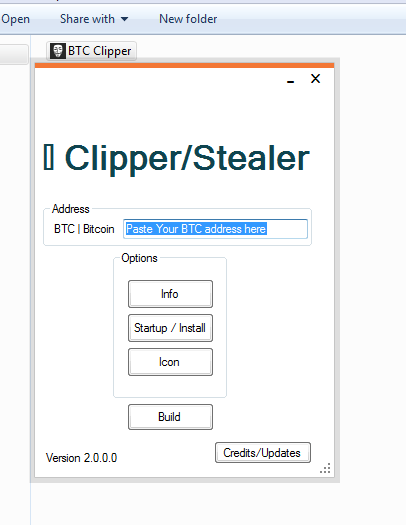
XMR Clipping and Stealing
LTC Clipping and Stealing
BCH Clipping and Stealing
BTC Clipping and Stealing
ZCASH Clipping and Stealing
DOGE Clipping and Stealing
ETH Clipping and Stealing
UAC BYPASS
START UP
START UP TASK MANAGER
START UP SCHEDULER
START UP REGISTRY EDITOR
SKIP VMWARE VITUAL BOX ETC
PROPERTIES
ICON CHANGING SUPPRT
Whatsapp
Discord: blackhatrussiaofficial#5904
Telegram: https://t.me/adrikadi
Download Shark Crypto Clipper
Shark Crypto Clipper
Shark Crypto Clipper Download Link