Zeus RAT 2025

The Zeus Remote Access Trojan (RAT), also known as Zbot, has been a persistent threat in the cybersecurity landscape since its emergence in 2007. Initially designed as a banking Trojan to steal financial credentials, Zeus has evolved significantly, spawning numerous variants and adapting to modern security measures. As of 2025, while the original Zeus malware is less prevalent, its legacy continues through its source code, which was leaked in 2011, and its influence on newer malware strains. This article explores the current state of Zeus RAT, recent developments, and strategies to mitigate its risks.
Historical Context
Zeus first gained notoriety for targeting Microsoft Windows systems, using techniques like man-in-the-browser attacks, keystroke logging, and form grabbing to steal sensitive data, particularly banking credentials. Its ability to create botnets—networks of compromised devices controlled by a command-and-control (C&C) server—made it a favorite among cybercriminals. By 2009, Zeus had infected millions of devices, compromising systems at organizations like Bank of America, NASA, and Amazon.
In 2010, the Zeus creator, reportedly Evgeniy Bogachev (aka “Slavic”), announced his retirement and handed the source code to the developers of the SpyEye Trojan. However, the 2011 leak of Zeus’s source code to the public fueled the creation of variants like GameOver Zeus, Ice IX, and Carberp, each introducing new capabilities such as ransomware and peer-to-peer (P2P) communication.
Zeus RAT in 2025: Current Landscape
While the original Zeus Trojan is no longer a dominant threat, its influence persists in 2025 through its variants and the broader malware ecosystem. The public availability of its source code has democratized access, allowing less-skilled cybercriminals to adapt Zeus’s techniques. Below are key developments and trends related to Zeus RAT in 2025:
1. Evolution of Variants
Zeus’s variants, such as GameOver Zeus, continue to pose risks. GameOver Zeus, which emerged in 2011, introduced a decentralized P2P architecture, making it harder to dismantle than traditional C&C-based botnets. In 2025, remnants of GameOver Zeus and similar variants are still detected in targeted campaigns, often combined with ransomware like CryptoLocker to maximize profits.
Newer malware strains, like Remcos and Xeno RAT, have drawn inspiration from Zeus’s modular design and stealth capabilities. For instance, Remcos, a RAT active since 2016, employs tactics like screen capture and keylogging, reminiscent of Zeus, and has climbed to prominence in 2023–2024 threat indices.
2. Delivery Methods
Zeus and its successors rely on sophisticated delivery mechanisms:
Phishing Campaigns: Spam emails and social media messages remain primary vectors, often tricking users into clicking malicious links or downloading infected attachments. Zeus variants can hijack legitimate email and social media accounts to send convincing messages.
Drive-by Downloads: Compromised websites exploit browser vulnerabilities to install malware without user interaction. While modern browsers like Google Chrome block many such attacks, older systems or unpatched browsers remain vulnerable.
Trojanized Applications: Malware is embedded in seemingly legitimate software, a tactic seen in recent RATs like Neptune RAT, which shares Zeus’s stealthy distribution methods.
3. Advanced Evasion Techniques
Zeus’s developers pioneered evasion techniques that continue to influence modern RATs:
Polymorphic Encryption: Zeus 1.4 introduced polymorphic encryption, allowing each infection to use unique file names and encryption keys, complicating antivirus detection.
Anti-Debugging: Modern RATs inspired by Zeus, such as Xeno RAT, check for debuggers and analysis tools before executing, ensuring stealth.
Fileless Malware: Some Zeus variants operate as fileless malware, residing in memory to avoid detection by traditional antivirus software.
4. Mobile Device Targeting
Originally focused on Windows, Zeus variants have expanded to mobile platforms. By 2025, malware inspired by Zeus targets Android and other mobile operating systems, aiming to bypass two-factor authentication (2FA) and steal mobile transaction authentication numbers (mTANs). This trend reflects the growing use of mobile banking and the need for cross-platform malware.
Recent Developments in 2025
While no major Zeus-specific campaigns have dominated headlines in 2025, the broader RAT landscape shows its enduring influence:
Open-Source Malware Proliferation: The availability of Zeus’s source code on platforms like GitHub has lowered the barrier to entry for cybercriminals. For example, Xeno RAT, released as an open-source project in 2024, incorporates Zeus-like features such as hidden virtual network computing (hVNC) and SOCKS5 proxy capabilities.
Integration with Ransomware: Zeus’s association with ransomware, notably CryptoLocker, continues in 2025. Attackers combine credential theft with file encryption to pressure victims into paying ransoms, a strategy refined by GameOver Zeus.
Targeted Attacks: While Zeus was historically broad in scope, modern RATs inspired by it focus on high-value targets like government agencies and financial institutions. For instance, Neptune RAT, reported in April 2025, targets Windows users to steal credentials from over 270 applications, echoing Zeus’s data-theft focus.
Impact and Scale
The Zeus Trojan and its variants have caused significant financial damage. At its peak (2011–2014), Zeus infected over 1.2 million computers, with GameOver Zeus alone responsible for over $100 million in losses. The FBI estimated that 40% of CryptoLocker victims paid ransoms, contributing to $27 million in illicit revenue. In 2025, while direct Zeus infections are rare, its techniques underpin many active threats, amplifying the global cost of cybercrime.
Mitigation Strategies
Protecting against Zeus-inspired RATs in 2025 requires a multi-layered approach:
User Education: Train employees and individuals to recognize phishing emails and avoid suspicious links or attachments. Security awareness programs can reduce the success rate of social engineering attacks.
Endpoint Protection: Deploy advanced antivirus and endpoint detection and response (EDR) solutions, such as Cynet 360 or CrowdStrike Falcon, to detect fileless malware and anomalous behavior.
Patch Management: Regularly update operating systems, browsers, and applications to close vulnerabilities exploited by drive-by downloads.
Network Monitoring: Implement firewalls and behavior-based monitoring to block outbound communication to known C&C servers. Application whitelisting can prevent unauthorized executables from running.
Mobile Security: Use reputable mobile security apps and enable 2FA to protect against mobile-targeted variants. Avoid downloading apps from unverified sources.
Incident Response: Develop a comprehensive incident response plan to isolate infected systems and mitigate damage. Regular vulnerability assessments and penetration testing can identify weaknesses.
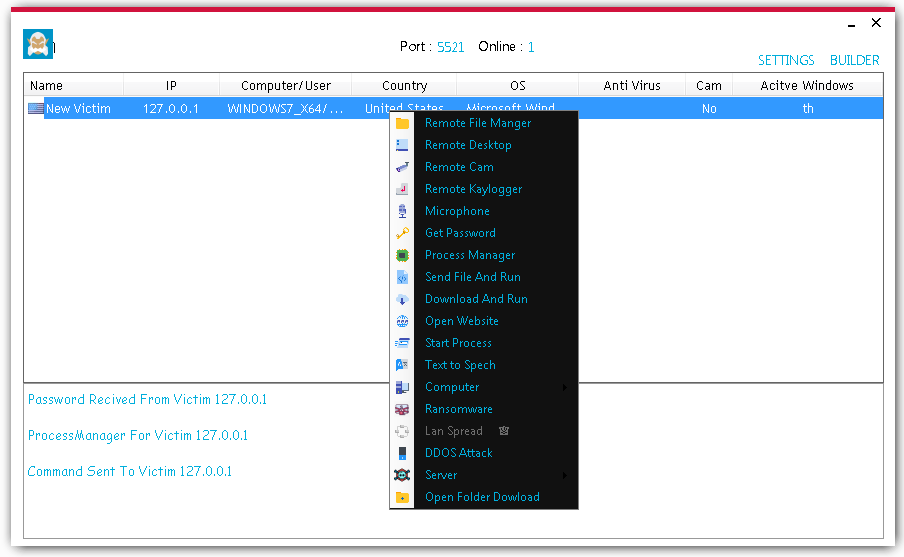
Remote File Manager
Remote Desktop
Remote Cam
Remote Keylogger
Microphone recording
Password Grabbing
Keylogger
Process Manager
Send File and Run
Download and RUn
Open Website
Start Process
Text To Speech
Computer
Ransomware
DDOS attack
Server Control